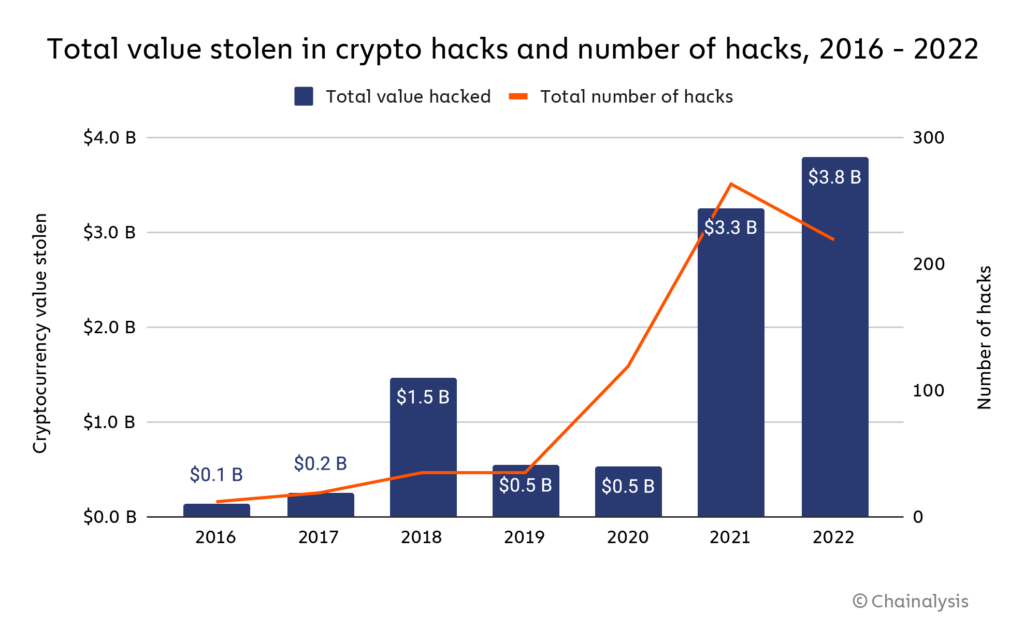
Cyber criminals stole a staggering US$3.8 billion from cryptocurrency businesses in 2022, up from an already high US$3.3 billion a year ago, by doubling down on successful hacking methods, according to Chainalysis.
The most common way to get to unsuspecting victims now, the blockchain data platform notes, is by hacking into the open DeFi protocols used by many crypto businesses.
For example, protocols used to enable users to port their cryptocurrencies from one blockchain to another are an attractive target.
The underlying smart contracts that enable transactions to go through automatically could hold errors in their code or weak spots, which can be exploited by hackers to steal digital assets.
Such “cross-chain bridges” account for 64 per cent of all DeFi protocol hacks, which themselves accounted for 82.1 per cent of all cryptocurrency stolen by hackers last year, according to Chainalysis.
In the same way vulnerabilities in crypto exchanges were the most attractive to hackers in 2019, today the malicious actors are targeting any loopholes in the DeFi protocols used commonly by users, said Kimberly Grauer, director of research at Chainalysis.
While 2021 was the first time such DeFi protocol hacks became the most common way to steal cryptocurrency, the threat deepened in 2022 because hackers doubled down on the effective practice, she explained, during an online webinar today.
The chief culprits, according to Chainalysis, are North Korean hackers from the Lazarus Group, who also made use of mixers to transfer stolen funds and hide their tracks.
Mixers are programs that help anonymise cryptocurrency transactions by mixing different funds to make it hard for each of the funds to be identifiable. They have been accused of being used to launder money.
Indeed, Grauer said North Korean hackers were reliant on mixers such as Tornado Cash, which was sanctioned by the United States government last year, to launder their loot.
However, she noted that there were other mixers that are still in existence, which hackers can still access.
To ward off DeFi protocol attacks, Chainalysis recommends that developers simulate attacks to find vulnerabilities, monitor for suspicious activity on the smart contracts and automate processes that can pause their protocols and halt transactions should suspicious activity occur.